Staying safe in your inbox is challenging; so challenging in fact that in 2020, 97% of users were unable to recognize a sophisticated phishing email.
WHAT’S THE RISK?
- 22% of all data breaches (in 2020) involved phishing attacks.
- The average loss of a spear phishing attack (in 2020) was $1.6 million USD.
- 78% of users claim to be familiar with the risks of unsolicited links in emails. And yet, they click on the links anyway.
- 1 in every 8 employees shares information on a phishing site.
- 1 in every 2 organizations was targeted by a ransomware attack in 2019. Data was successfully encrypted by attackers in 73% of these attacks.
- 1 in every 3 companies that suffered a ransomware attack paid the ransom and the average ransom demand is nearly $84,000 USD.
With a risk this great to your business, you need to know what phishing is and how to protect against it!


Phishing is when someone tries to trick you into divulging sensitive information or data by impersonating a trustworthy entity.
The phisher’s attempts may look like a harmless log-in notification email or even a simple request from a “colleague” to name a few, but these ARE attempts to steal your information and we’re here to show you our top three tips for staying safe in your inbox.
Read on to learn more, or take just 4 minutes out of your day to watch the video below!
Tip 1: Always Check the Source
Be sure to check the email address or phone number, because these CAN be trick to spot. Even just one changed number or letter can mean the difference between business as usual and a data breach. Take this example below:


We’ve seen multiple phishing attempts like this one! Cybercriminals rely on human nature, assuming you WON’T check minor details like a single letter’s difference. Now you know you must stay vigilant.
Also, if you ever have any doubts about a text or email, check with the original sender via phone call or message through your team’s communication platform to verify the message origin.
Lastly, if there is ever money involved, always verify with a conversation. Wherever money is concerned, it’s better to be safe than sorry.
Tip 2: Check Links Before Clicking Them
On a desktop it’s quite easy: hover your mouse over the link and a little pop-up will appear at the bottom corner of the window. We’re using this blog post in the example below, but the same is true for email in that the link will appear in the bottom corner of your screen, just like where we’ve highlighted in red:
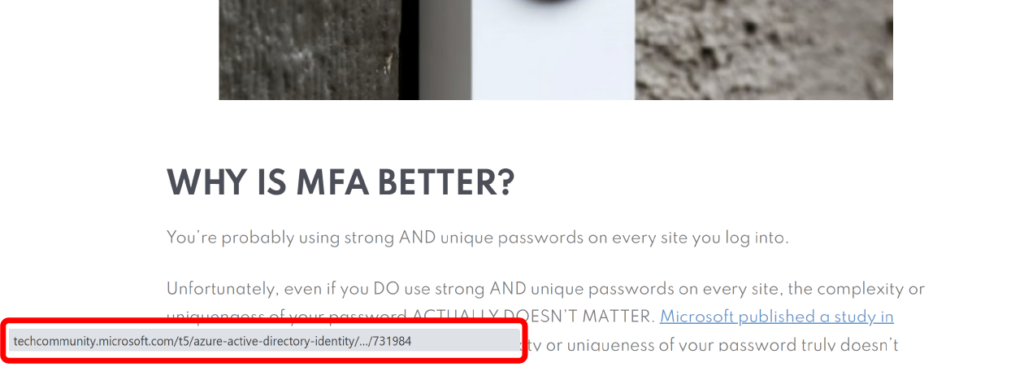

It’s trickier to check links on your phone, but there IS a way: Copy the link address and paste it into a note app to see the address url. If it’s not a website or URL that you can easily understand or identify, it’s better to not visit the page.
Regardless of on your phone or desktop, in all cases we always want a “better safe than sorry” approach!
Tip 3: Check the Destination
Double-check the “to” field in your email to make sure everything is correct.
And ESPECIALLY check the URL address before you log in to a page! Hackers can create fake websites that look exactly like login pages to popular platforms like Google, Facebook, and LinkedIn.
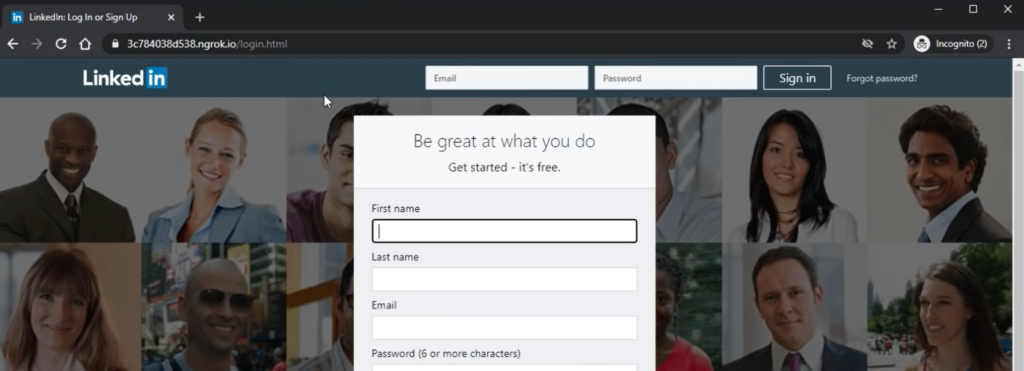

If you look closely at the example above, you’ll see the URL is NOT linkedin.com but an odd sequence of letters and numbers. If you “logged in” to this website, your login information would be sent to the hackers who created that website instead!
WRAPPING UP
These tips are just part of the recipe required to protect your inbox, your people, and your business from cyber security threats. We’ve published our top recommendations for protecting your organization from a data breach which you can read about here.
Or better yet, download a copy of our e-book on the Top 12 Cybersecurity Tips to Reduce Business Risk.
Phishing isn’t the only cyberthreat to watch out for, but this is a great first step to making your business more secure. Looking for help protecting your organization? We can help
RELATED BLOG POSTS

What is MFA?
While there's no such thing as 100% protection in cybersecurity, MFA hits pretty darn close to where account security is concerned! It drastically improves the security of ANY asset, digital or otherwise, and it's one of the easiest to implement. Read more about it today!


7 Best IT Practices
IT is easy to manage when you’re a business of one. But as your business grows and evolves, things get harder. Keep these seven best practices in mind when it comes to navigating IT for your business and you’re going to be in a better place!


Recognize a Cyberattack
We always want to focus on proactive cybersecurity measures, but just as important is how to recognize a cyberattack while it’s occurring! That’s why we’re covering 5 areas of your business that could be compromised and the key signs you should look out for!

