In this follow-up to our Cybersecurity 101 webinar, we cover 5 types of cyberattacks businesses should be aware of, the costs involved, real-life examples of each attack, and some best practices you can use to keep your business safe.
It’s important to know about cyberattacks because they happen every day!
For example, did you know over 30,000 websites are hacked each day? That’s a website hacked every 39 seconds!
That’s why cybersecurity is critical to you and your business.
Defining Cybersecurity
In our Introduction to Cybersecurity webinar, we defined cybersecurity as
“How you protect your data, and information systems from cyberthreats and attacks.”
It’s also important to note that cyberattacks affect 3 key areas of your business:
- Your Revenue
- Your Data
- Your Reputation
Common Myths (and Truths) About Cybersecurity
Misinformation, lack of awareness, and ineffective training put businesses at risk every day, so we wanted to dispel some common myths around cybersecurity.


Myth 1: Big companies and wealthy people are more likely to be targeted by cyberattacks.
The truth is that it’s not about who you are, it’s about whether your information is valuable. Another truth, your information IS valuable, and you might not even realize it!
Myth 2: Your security software will always protect you
While security software should be part of your cybersecurity strategy, it shouldn’t be your only strategy. That’s because even security software companies can be hacked too, such as in 2019, where three top US antivirus companies were breached by a Russian hacking collective, who profited over $1 million USD from it.
Myth 3: Cyberthreats are always external
From Verizon’s 2021 Data Breach Investigations Report, insiders are responsible for around 22% of security incidents.
Myth 4: Your password will never be cracked
We discussed this myth in our webinar on making stronger passwords.
Your password WILL be hacked. It’s only a matter of time because hackers run billions of password combinations. That’s why we always recommend bolstering your login security with a secondary method like multi-factor authentication.
Myth 5: Cybersecurity is expensive to deploy and maintain
Have you ever heard of the saying “Penny-wise pound-foolish?”. That’s many people with cybersecurity: spend a little now, but pay an exorbitant amount later to recover, restore, or implement damage control on their data, information, and systems. Cybersecurity should be an investment in your business, not an after-thought purchase.
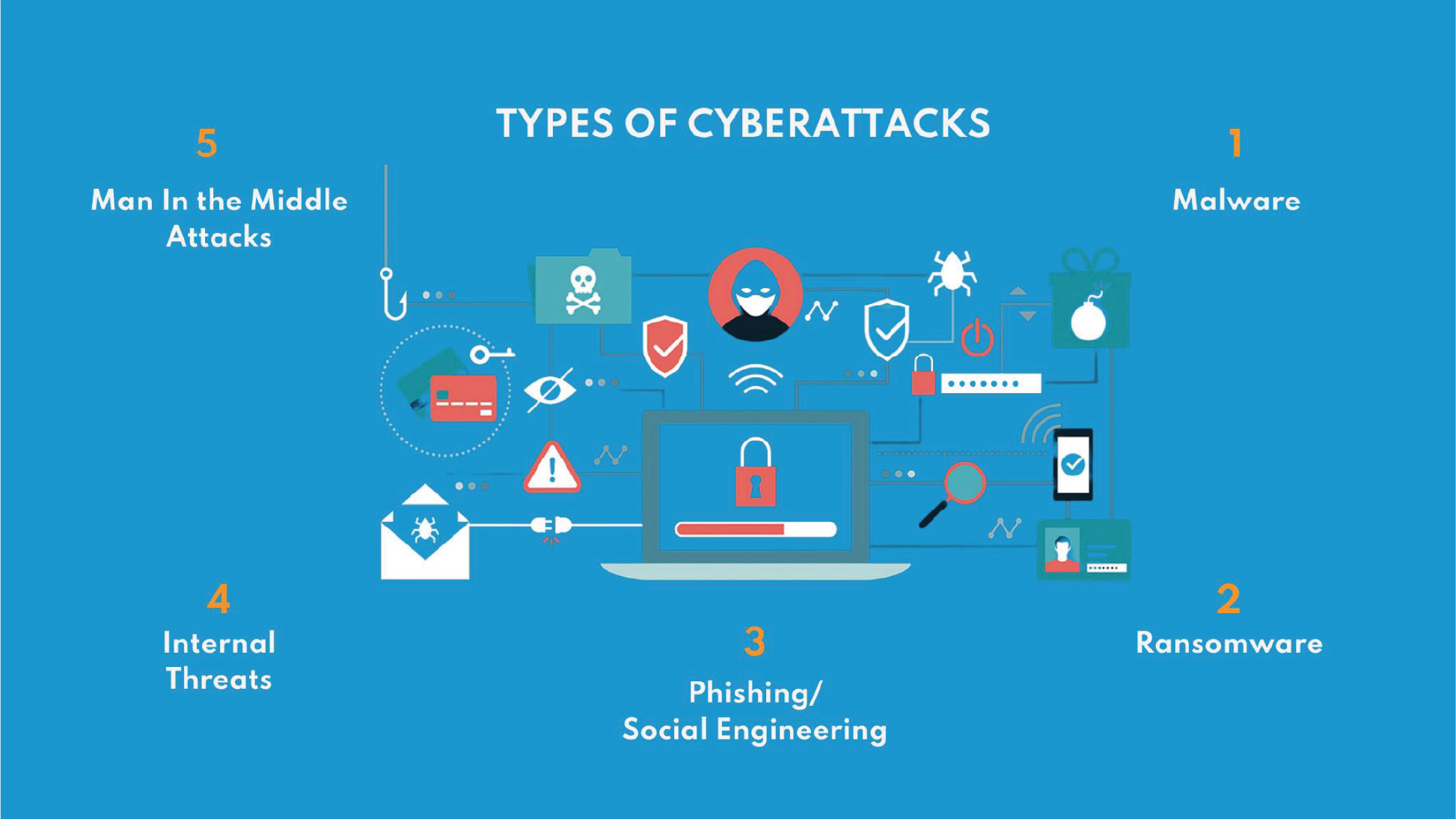
5 Types of Cyberattacks to Watch Out For
The 5 Cyberattacks to be wary of are:
- Malware
- Ransomware
- Phishing/Social Engineering
- Internal Threats
- Man In the Middle Attacks
We’ll briefly discuss what the attacks are, how they occur, some important statistics and information surrounding the attacks, and lastly examples of successful attacks using each.

Attack 1: Malware
What is it: A file or code that disrupts, damages, or gives access to your system.
How does it happen: It is contracted from downloading a program, opening or downloading attachments, or even clicking on links in emails/text messages.
Stats/Information: Malware is difficult to detect because it’s polymorphic, which means it can constantly change its code to evade detection.
Real-world example: In May 2021, Canada Post was the victim of a malware attack, affecting 950,000 parcels. Postal addresses, emails, and phone numbers were also exposed.
Attack 2: Ransomware
What is it: Software that attackers use to hold your system ransom until a sum of money is paid.
How does it happen: Ransomware encrypts your files and demands ransom payment for a decryption key. Attackers force organizations to pay the ransom to regain access to their files.
Stats/Information: Ransomware starts encrypting your files and locking you out of your system in as little as 3 seconds. Also, 82% of reported ransomware in 2021 affected organizations with less than 1000 employees.
Real-world example: cybercriminals attacked a small business with only 8 computers! Their insurance paid the $150,000 ransom because the alternative was to shut down the business.
Attack 3: Phishing/Social Engineering
What is it: A scam where attackers impersonate a legitimate company or person asking for sensitive information.
How does it happen: It can look like a “vendor” claiming there’s problems with your payment information, including a fake invoice with it. They might want you to click a link to make a payment. We go through several phishing examples here.
Stats/Information: Phishing emails sent globally have increased by 667%! 70% to 90% of all data infiltration is due to phishing and social engineering attacks.
Real-world example: Posing as the CEO, an attacker emails a manager using a subject line that looks legitimate. The manager clicks on a link that redirects to a spoofed version of an invoice, and the attacker steals his credentials gaining full access to their network.
Attack 4: Internal Threats
What is it: An insider who uses their authorized access, willingly or unwillingly, to do harm to a company’s system.
How does it happen: It may look like activity at unusual times—signing into the network at 3 am; high volume of traffic—transferring too much data via the network; suspicious activity—accessing unusual resources.
Stats/Information: Companies from North America suffer the most from insider attacks and their consequences with an average cost of $13.3M. Further to that, 98% of organizations feel vulnerable to insider attacks.
Real-world example: In 2021, a Pfizer employee uploaded 12,000 confidential files to her Google Drive account from her corporate laptop. She shared confidential documents including drug development data and trade secrets related to the COVID-19 vaccine and its studies.
Attack 5: Man-in-the-Middle Attacks
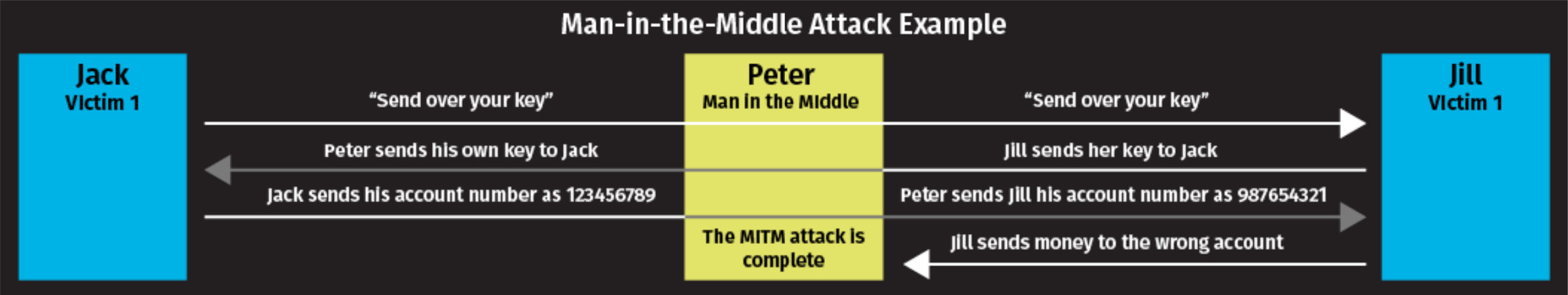

What is it: An eavesdropping attack where cybercriminals intercept and relay messages between two parties to steal data.
How does it happen: The hacker sets up a false Wi-Fi network. Meanwhile, the hacker can note down passwords, usernames, and any private data users enter while on their network.
Stats/Information: Attackers sent over 30 emails to disrupt a financial transaction worth $1M. By impersonating users and modifying banking details, funds were transferred to the attackers’ account.
Real-world example: In a wire-transfer heist, an attacker used unique tactics—including communicating through email and even cancelling a critical in-person meeting–to fool both parties on either end of the transfer.
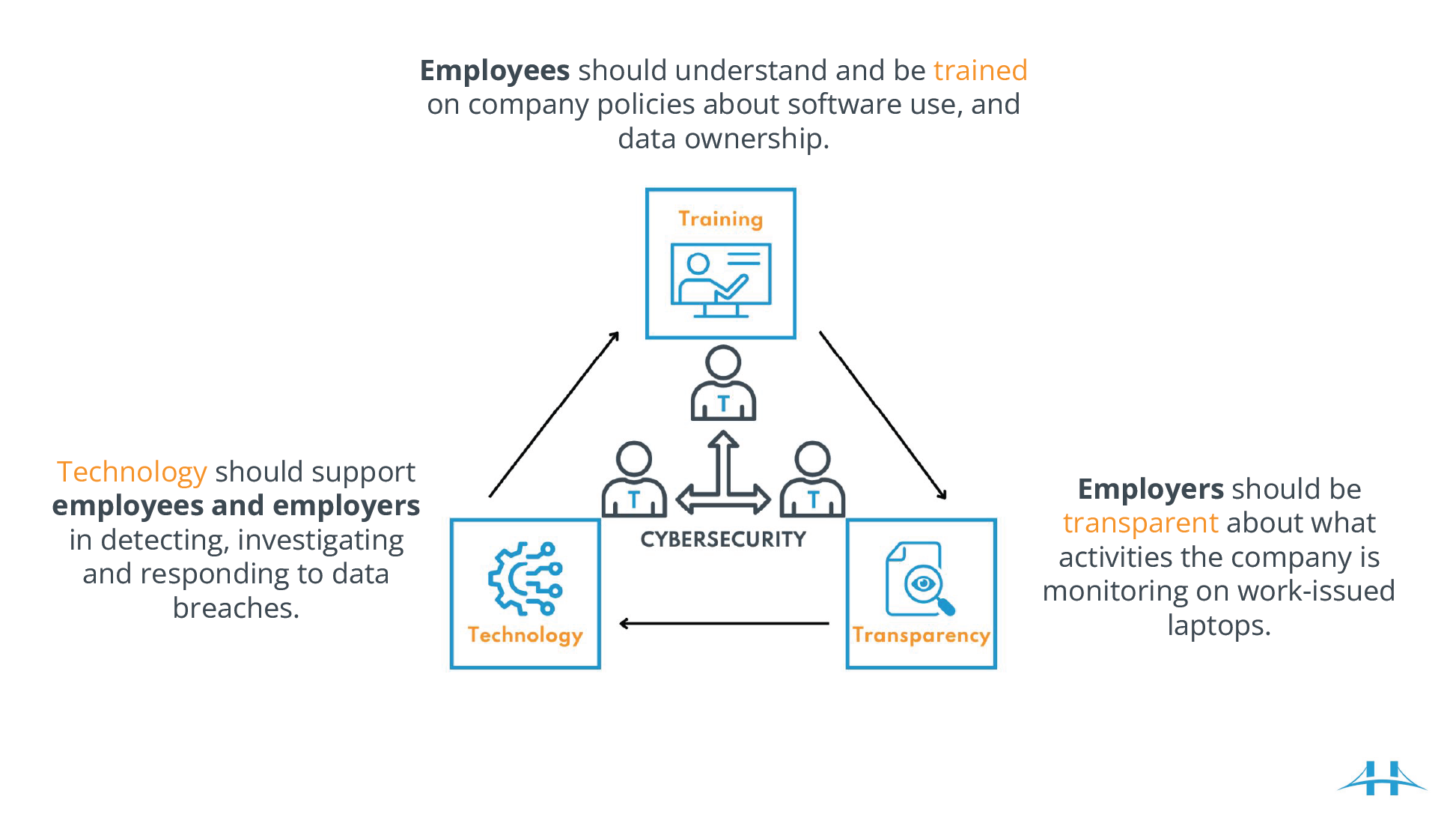
How to Protect Yourself and Your Business
In order to protect your business, follow the three Ts!
Employees should understand and be trained on company policies about software use, and data ownership.
Employers should be transparent about what activities the company is monitoring on work-issued laptops.
Technology should support employees and employers in detecting, investigating and responding to data breaches.

Top Tips for Your Safety
The three Ts are just one step of many you can take to improve your cybersecurity! Here’s a few more practical tips you can use every day:
1. Be SENSIBLE – Never click on links, download files or open attachments in emails (or on social media) that aren’t from a known, trusted source.
2. Be PROACTIVE – Learn as much as possible about cybersecurity, get certified, and ask for training at the workplace.
3. Be VIGILANT – Every situation you come across could be a potential scam. It’s better to be safe than sorry.
Don’t worry if you can’t remember all this information: we’ve summarized it in our one-pager down below.


At Clearbridge Business Solutions, we’re dedicated to equipping our customers with the tools they need to be more cyber secure through managed IT services and educational resources.
We can only cover so much in a webinar. If you’re ready for a partner to come alongside you for all your IT strategy, IT security, and IT support needs then get in touch today!


Cybersecurity 101
You’ve heard people using the term “cybersecurity” for a while now, but what exactly does it mean? We’re here to help you understand cybersecurity and why you should care about it…without getting too technical.


Public Wi-Fi Safety
When you work or travel anywhere that isn’t your office or home, you connect to the Wi-Fi networks easily available to you. But you need to be wary, because not every network is safe!


What is ClearOne?
Clearbridge Business Solutions provides technology services to businesses in a few unique ways. ClearOne is our most comprehensive offering spanning all technology facets in your business.

